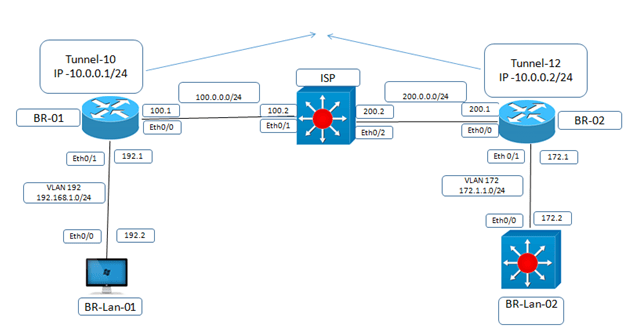
As per the topology above, Let's understand and configure site-to-site VPN based on these tasks
Tasks
● Configure R1 AS Branch-01 router with ip address of 100.0.0.1/24 and 192.168.1.1/24 on 0/1 and create tunnel interface 10 with ip address 10.0.0.1/24 and tunnel destination would be 200.0.0.1
● Configure R2 AS Branch-02 router with ip address of 200.0.0.1/24 and 172.1.1.1/24 on 0/1 and create tunnel interface 12 with ip address 10.0.0.2/24 and tunnel destination would be 100.0.0.1
● Create site to site VPN tunnel b/w gre tunnel 10 and gre tunnel 12 using pre shared key unnets@123
● Verify from tunnel 10 to tunnel 12
Explanation
Site-to-Site IPSec VPN Tunnels are used to allow the secure transmission of data, voice and video between two sites (e.g offices or branches). The VPN tunnel is created over the Internet public network and encrypted using a number of advanced encryption algorithms to provide confidentiality of the data transmitted between the two sites.
This article will show how to setup and configure two Cisco routers to create a permanent secure site-to-site VPN tunnel over the Internet, using the IP Security (IPSec) protocol. In this article we assume both Cisco routers have a static public IP address. Readers interested in configuring support for dynamic public IP address endpoint routers can refer to our Configuring Site to Site IPSec VPN with Dynamic IP Endpoint Cisco Routers article.
IPSec VPN tunnels can also be configured using GRE (Generic Routing Encapsulation) Tunnels with IPSec. GRE tunnels greatly simply the configuration and administration of VPN tunnels and are covered in our Configuring Point-to-Point GRE VPN Tunnels article. Lastly, DMVPNs – a new VPN trend that provide major flexibility and almost no administration overhead can also be examined by reading our Understanding Cisco Dynamic Multipoint VPN (DMVPN), Dynamic Multipoint VPN (DMVPN) Deployment Models & Architectures and Configuring Cisco Dynamic Multipoint VPN (DMVPN) – Hub, Spokes , m GRE Protection and Routing – DMVPN Configuration articles.
ISAKMP (Internet Security Association and Key Management Protocol) and IPSec are essential to building and encrypting the VPN tunnel. ISAKMP, also called IKE (Internet Key Exchange), is the negotiation protocol that allows two hosts to agree on how to build an IPSec security association. ISAKMP negotiation consists of two phases: Phase 1 and Phase 2.
Phase 1 creates the first tunnel, which protects later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data. IPSec then comes into play to encrypt the data using encryption algorithms and provides authentication, encryption and anti-replay services.
As GRE does not have its own mechanism to encrypt traffic it depends on IPSec for getting the encryption job done. As opposed to GRE over IPSec, which encrypts anything that is encapsulated by GRE, IPSec over GRE encrypts only the payload and not the routing protocols running over a GRE tunnel.
In IPSec over GRE, the GRE tunnel is established over the internet, neighbor ship is formed and routes are exchanged and all of this is in clear text. We are only concerned with encrypting the interesting traffic flowing between the two peers. When securing the routing updates and routes isn’t a requirement and the major concern is to encrypt the information/payload flowing between the peers we use IPSec over GRE.
IPSec over GRE eliminates the additional overhead of encrypting the GRE header.
Configuration
Comments (0)
Categories
Popular posts

Cisco Nexus Port Channel: Configuring ...
24 Apr 2024
Configure Rapid PVST on Cisco Nexus
5 Apr 2024
Palo Alto Exam Cost: PCNSA, PCNSE & More
28 Mar 2024
Cisco ACI VPC Configuration Task Steps
6 Jan 2024Recent posts
Network Hardware Devices: Explained
24 Apr 2024
Palo Alto Firewall Certification ...
24 Apr 2024
AWS Certification Path: Amazon Cloud
24 Apr 2024
Cisco Nexus Port Channel: Configuring ...
24 Apr 2024



