Task
● Understanding of users authentication and identity management
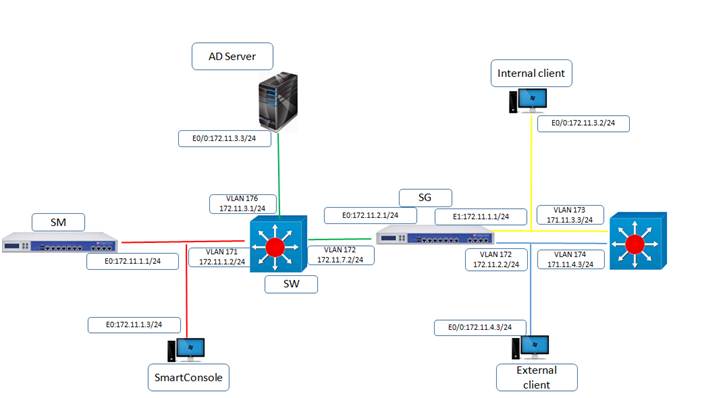
● Perform telnet authentication from internal client (172.11.3.3) to external client (172.11.4.3) using legacy authentication method is user authentication and authentication scheme is checkpoint password and username is Uninets and password is admin123
● Manage users to access to different services like https ,ssh by using external database using LDAP and ip address of Ad server is 172.11.3.3
Explanation
Checkpoint point authentication features enables you to verify the identity of users logging into the security Gateways but also allow you to control security by allowing some users or disallowing some others for that some authentication scheme has been specified such as LADAP , RADIUS ,SECURE ID,TACACS
Creating Users and Groups
Authentication rule has been defined by user groups not by individual users therefore you must first define users and then add them to groups to define authentication rules you can define users using the security gateway proprietary user database or using an LDAP, radius servers
User Type
External User profile: – Externally defined users .who are not defined in the internal users database or External users are authenticated based on either their name or their domain
LDAP Groups: – LDAP groups are required for performing a variety of operations such as defining LDAP user’s access rule or LADP remote access communities
Templates: – It facilitates the user definition process and prevents mistakes by allowing you to create new users based on the appropriate template and change only a few relevant properties as needed
Users Groups: – Users groups are collection of users and sub users groups we utilize it for different purpose such as vpns and local
Database management
Users: – These are either local clients or remotes clients, who can access your network and resources
Type of legacy authentication:-
User authentication:- its uses for per user basis authentication so its uses services like http, https and ftp, telnet its user is secure because authentication valid for one connection only
Session authentication: – Provide authentication mechanism for any service and requires users to supply their credential for each authentication session for session authentication agent must be installed on every authenticating client therefore this method is not suitable for authenticating http services as they open multiple connection per sessions
Client authentication :- permits multiple users and connections from the authorized ip address or host authorization is performed per machine for example if finger is authorized for client machine all users on the client are authorized to use finger and not asked to supply password
Authentication scheme:-
Checkpoint password: – the security gateway can store a static password in the local user database of each user configured on the security management server
Operating system password: – security gateway can authenticate using the username and password that is stored on the operating system of the system like Gia os
Radius: – it’s an external authentication scheme that provides security and scalability by separating the authentication function from the access server using radius radius uses UDP to communicate security gateway
TACACS: – it’s also a external-authentication scheme that provides verification services .its provide access control for routers and network servers
Configuration
First log in into smart view tracker then select the firewall
Then double click on it
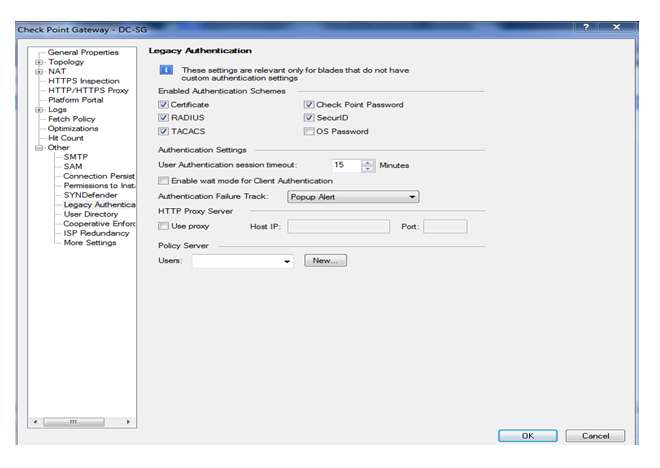
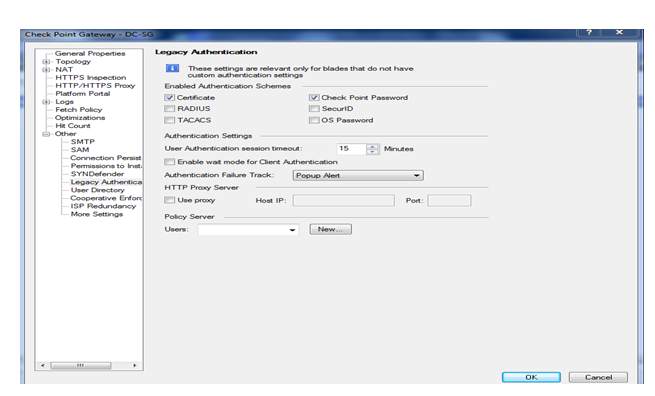
So here we can see by default all legacy method is selected but here are performing only check-point password so we need to select check-point password then click on ok
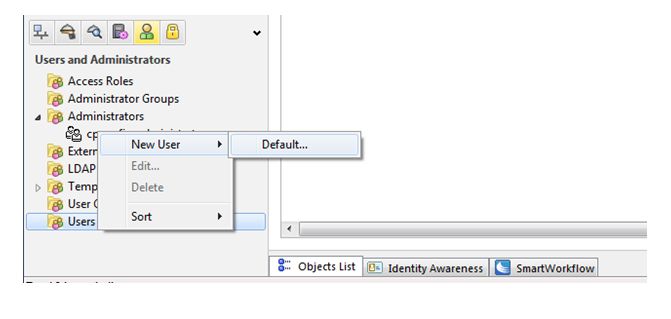
Now we to add a user so click on users and administrator tab and select users
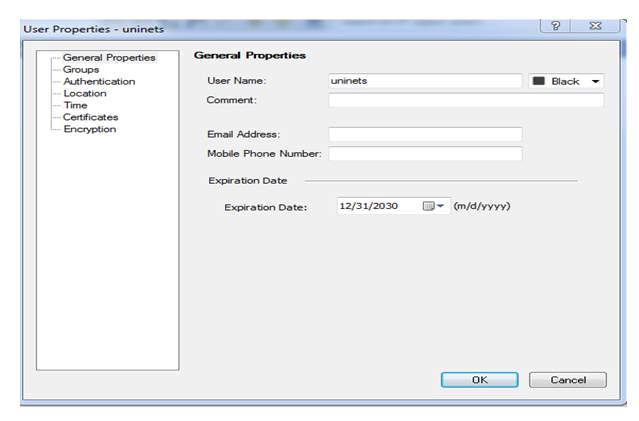
Here we defining username is Uninets now we have to select authentication method click on authentication tab
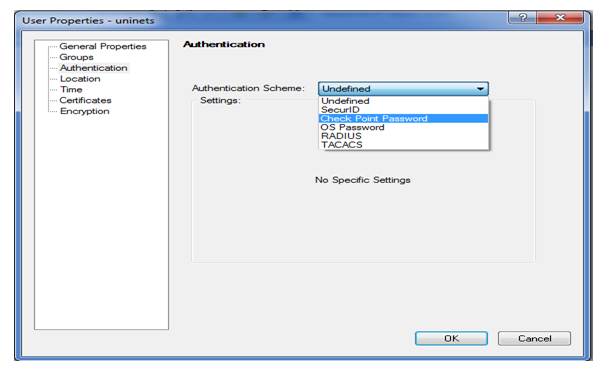
Here we can see we have multiple authentication schemes and we have select check point password
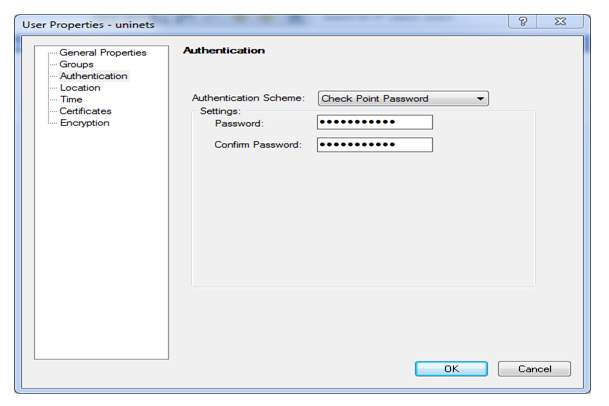
Here we selected authentication scheme is checkpoint password and we also providing password is admin123 as we earlier in task
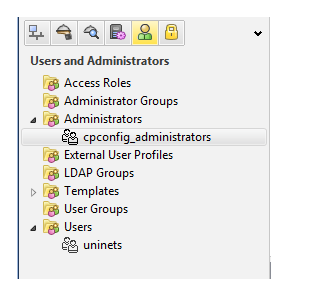
here we can a user has been created Uninets Now we have to create a user group as we earlier we can’t bind directly single user so we will create user-group tel-auth and add user Uninets
Now we have to click on new group
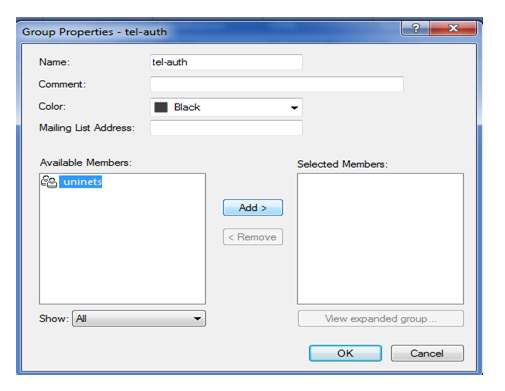
Now we selected user is Uninets and click on add and then click on ok
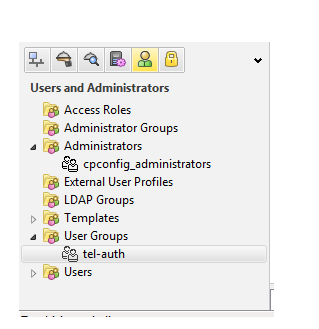
Here we check that user-group tel-auth has been created now we have to create a rule base or policy for traffic flow through firewall can hit by that rule now click on policy
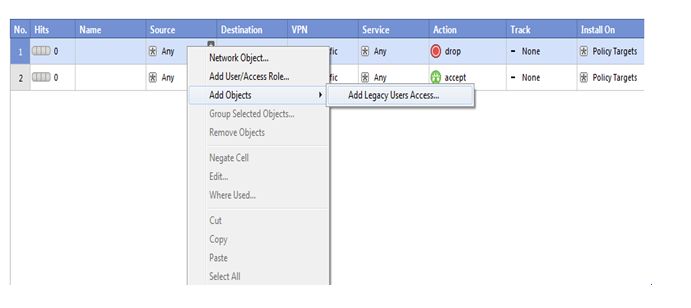
Now we have select source so right click on source-tab then click on add objects and then choose add legacy user’s access
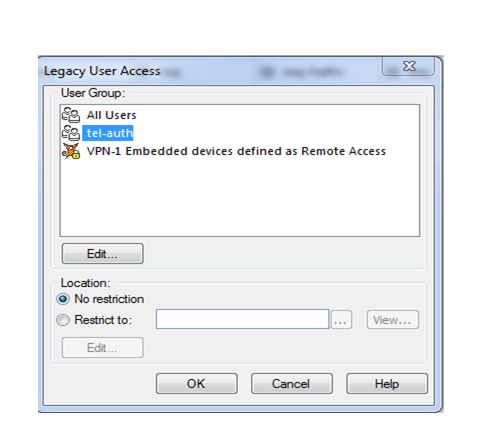
Here we select our created user-groups so as we know we earlier created tel-auth so select it and click on ok
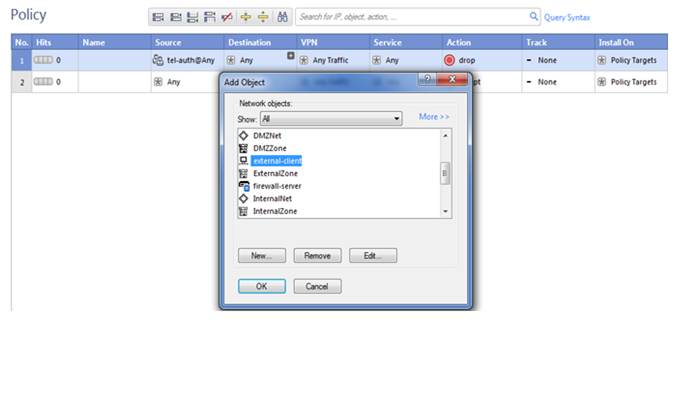
Now we are selecting here destination so our destination is external-client click on ok
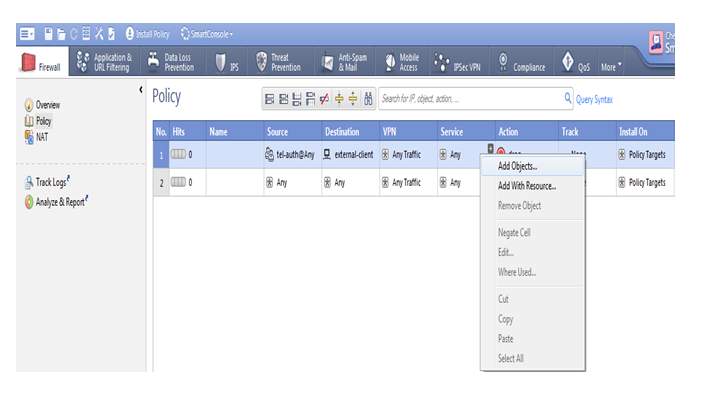
Here we are selecting service here click on add object then select telnet
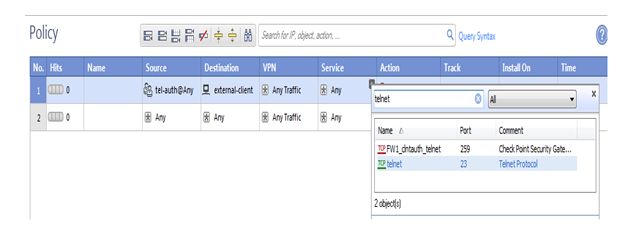
Click on ok
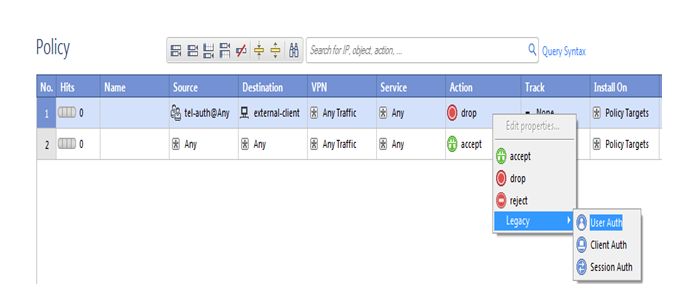
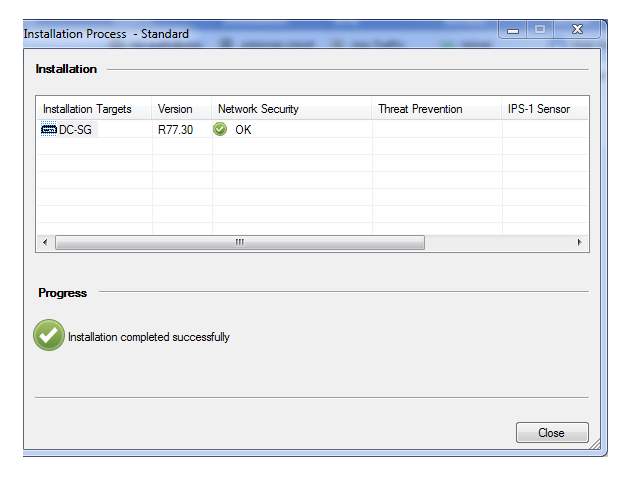
Now we add authentication scheme so click on legacy then choose User-auth then save the policy and push the policy on security gateway
Verification;-
dmz-cleint#
dmz-cleint#telnet 172.11.4.2
Trying 172.11.4.2 … Open
Check Point FireWall-1 authenticated Telnet server running on firewall-Gateway
Connected to 172.11.4.2
User Access Verification
Username: uninets
Password:
external-client>
here we can see that we authenticated through checkpoint firewall
Task: 02
Now we have from next task for that first we have to create a node for LDAP integration with win-server 2008 r2 we have a win sever ip is 172.11.3.3 so we have to create a node click on node and give name winserver-2008
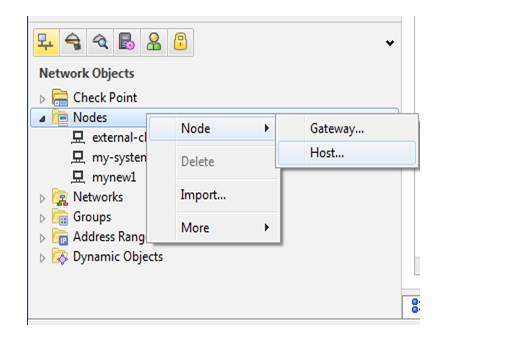
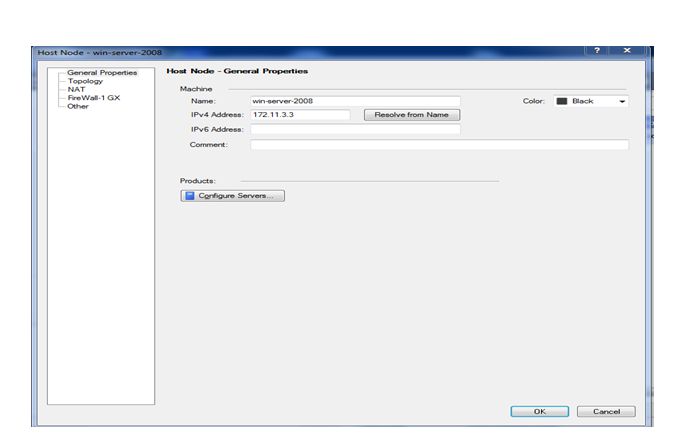
Now click on ok
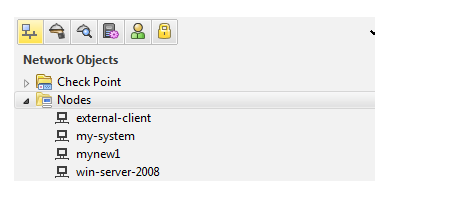
Here we can check that our new node has been created with the name of win-server-2008 now we have to create a ldap account unit for that click on servers and opsec tab
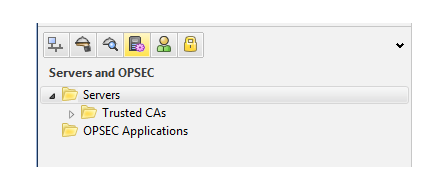
Now we have right click on servers
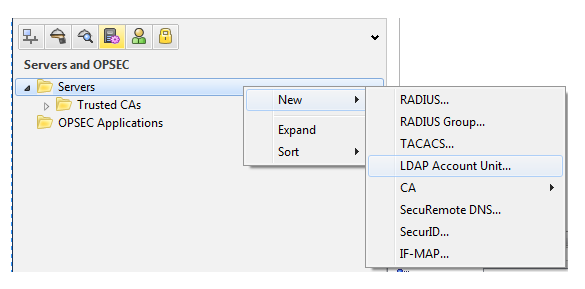
Then select new then there are so many servers then click on LDAP Account unit
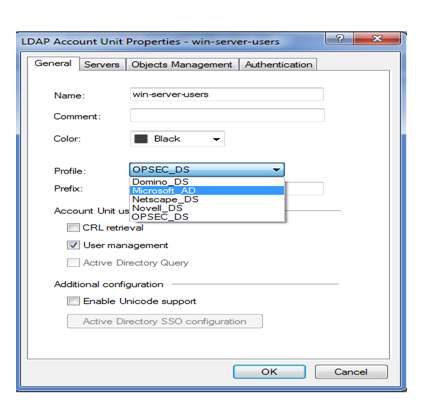
here we are a name to ldap account unit so we gave win-server-users then selecting profile means end server so here we are using Microsoft server then provide domain-name of server we already have a domain so here we mentioning a name is itnerds.com
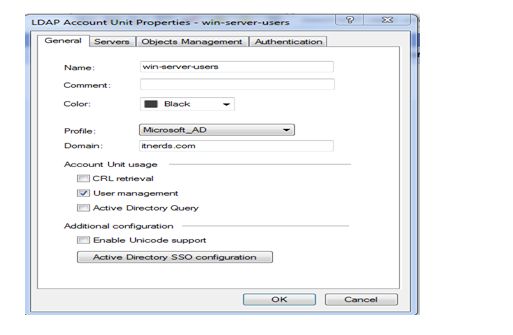
Here we given domain name is it nerds now click ok servers tab
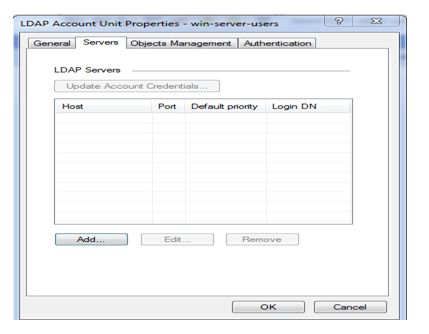
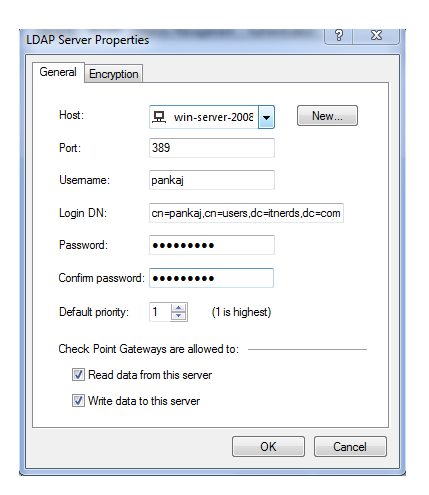
Now click on add to add first we have add host means a ip address of server as we know we already created a host for server
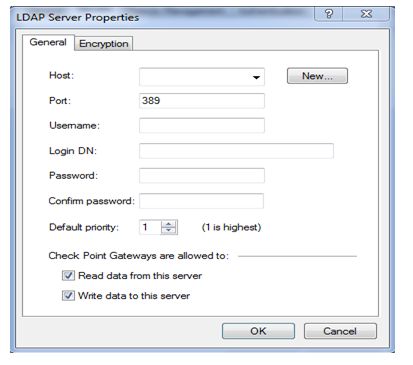
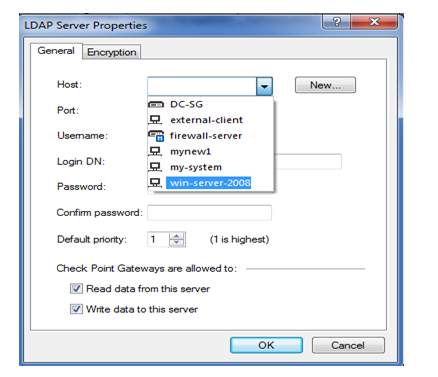
here selecting user is win-server-2008 then we have to provide username and login-dn and password for server access all details providing over here is related to server so for these details coordinate with server admin person
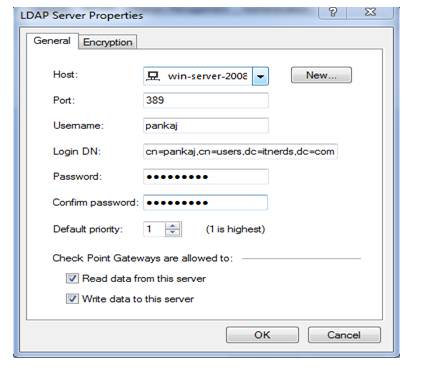
Click on ok
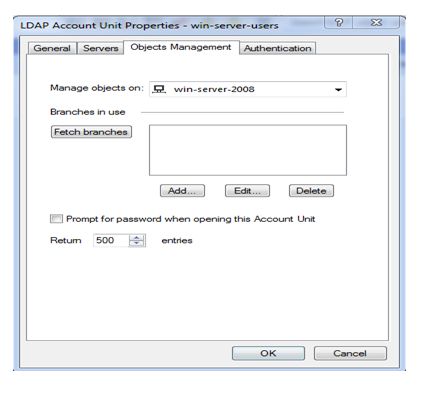
Now click on fetch branch and click on ok
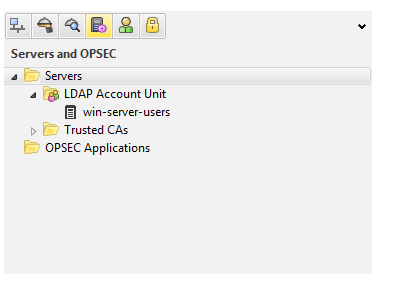
Here we see that once fetching has been completed LDAP account unit has been created now we have click on users that all server databases has been synced with SM
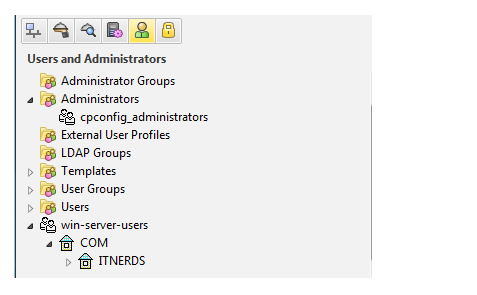
Here we seen that all database has been synced with security manager now we to create a LDAP-group to bind with policy we know that we can’t bind users directly with policy so create group with name of LDAP-GP
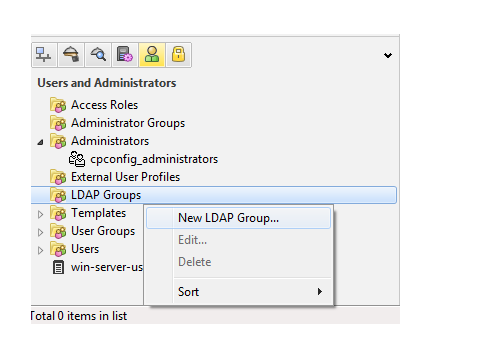
Click on new LDAP group
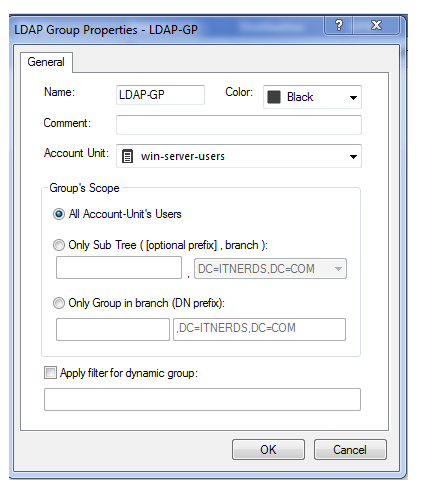
Here we have to provide name is LDAP_GP and account unit is win-server-users and click on ok
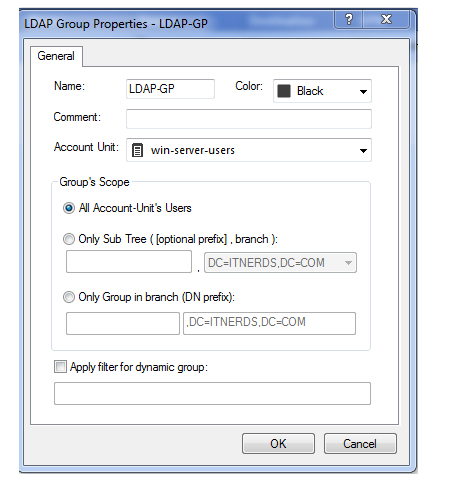
Here we can see that group has been created Now we have to create a policy then click on policy tab
Right click on source tab then select add objects then click on add Legacy Users
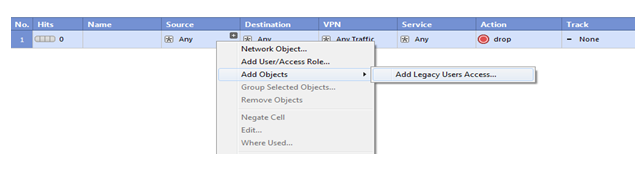
So choose LDAP-GP group and click on ok
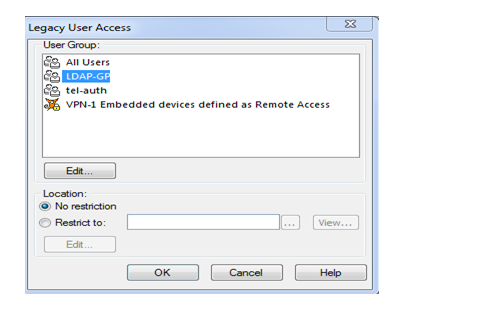
Need to bind authentication scheme so choose user-Auth and save the policy and push the policy on security gateway
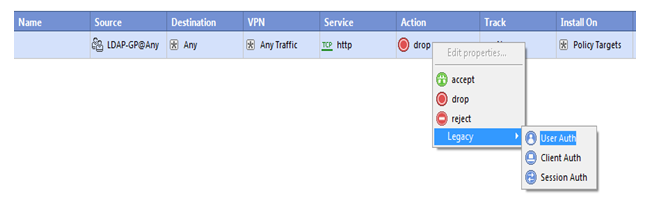
So policy has been pushed to security gateway
Verification;-
Here we see that it’s asking for username and password
Comments (0)
Categories
Popular posts

Cisco Nexus Port Channel: Configuring ...
22 Apr 2024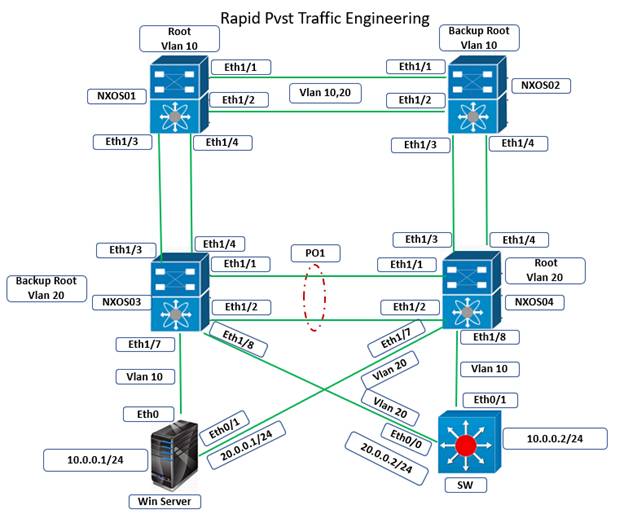
Configure Rapid PVST on Cisco Nexus
5 Apr 2024
Palo Alto Exam Cost: PCNSA, PCNSE & More
28 Mar 2024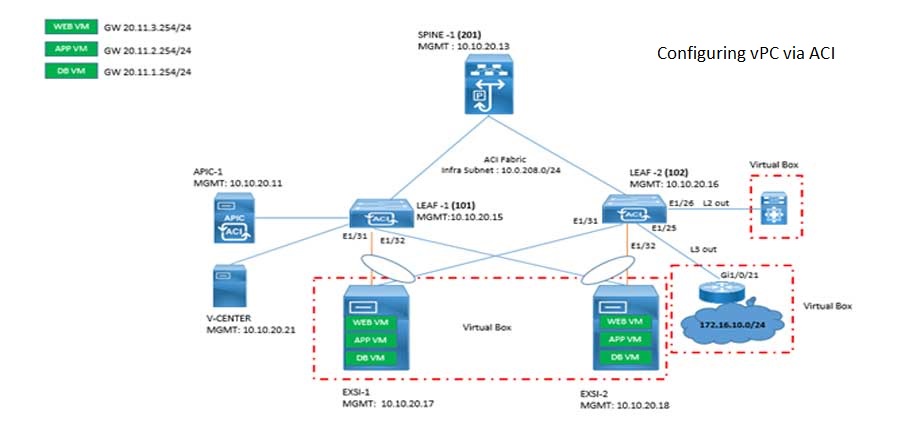
Cisco ACI VPC Configuration Task Steps
6 Jan 2024Recent posts
Network Hardware Devices: Explained
24 Apr 2024
CCNA Course Syllabus: Topics Explained
23 Apr 2024
AWS Certification Path: Amazon Cloud
23 Apr 2024
Cisco Nexus Port Channel: Configuring ...
22 Apr 2024