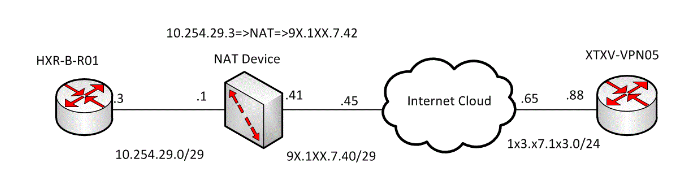
IPsec is a complex technology, and it becomes more complex when a NAT device is in the path between a site-to-site GRE over IPsec VPN. In my production environment a problem escalated to me stating that site to site IPsec tunnel had not been coming up. When I dig deep into it, I found that here is a firewall which was performing NAT on public IP address. First thing I did was to prepare a diagram of my own to understand the actual topology with IP addresses. Here is the topology diagram for the same with masked IPs.
Now after preparing the diagram my objective was clear. The objective was to establish a GRE over IPsec tunnel from STFV-VPN05 to HDR-B-R01. I followed the step-by-step approach in order to achieve the objective.
1. Configuring OR Verifying IP addresses
HDR-B-R01
interface GigabitEthernet0/0
ip address 10.254.29.3 255.255.255.248
STXV-VPN05
interface GigabitEthernet0/0
ip address 1×3.97.1×3.88 255.255.255.0
2. Configuring OR Verifying Routing
STFV-VPN05
Ip route 91.1xx.7.42 255.255.255.255 1×3.97.1×3.65 —Required reachability to public NATed
ip route 10.254.29.3 255.255.255.255 1×3.97.1×3.65 –require to find out going interface for Proxy ACL traffic in order to initiate GRE over IPsec traffic
STFV-VPN05#ping 91.1xx.7.42
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 91.1xx.7.42, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 68/76/80 ms
HDRBR01
ip route 0.0.0.0 0.0.0.0 10.254.29.1
3. Verifying IPsec Phase 1 and Phase2 Parameters
STFV-VPN05
crypto isakmp policy 9
hash md5
authentication pre-share
group 2
crypto isakmp key XXXX address 91.1xx.7.42
ip access-list extended Heidrun-Proxy-ACL
permit gre host 1×3.97.1×3.88 host 10.254.29.3
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
mode tunnel
crypto map MAP-TO-WORLD 10 ipsec-isakmp
set peer 91.1xx.7.42
set transform-set ESP-DES-MD5
match address Heidrun-Proxy-ACL
HDRBR01
crypto isakmp policy 8
hash md5
authentication pre-share
group 2
crypto isakmp key XXXX address 1×3.97.1×3.88
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
mode tunnel
ip access-list extended STFV-Proxy-ACL
permit gre host 10.254.29.3 host 1×3.97.1×3.88 —Proxy ACL must be inverse of the other end Proxy ACL
crypto map MAP-TO-FORUS 10 ipsec-isakmp
set peer 1×3.97.1×3.88
set transform-set ESP-DES-MD5
match address STFV-Proxy-ACL
4. Verifying OR Configuring GRE tunnels
STFVVPN05
interface Tunnel10
ip address 192.168.250.210 255.255.255.252
tunnel source 1×3.97.1×3.88
tunnel destination 10.254.29.3 —-IP address of the other end as tunnel destination
HDRBR01
interface Tunnel0
ip address 192.168.250.209 255.255.255.252
tunnel source 10.254.29.3
tunnel destination 1×3.97.1×3.88
5. Verifying OR Applying Crypto map on physical Interface
STFVVPN05
interface GigabitEthernet0/0
crypto map MAP-TO-WORLD
HDRBR01
interface GigabitEthernet0/0
crypto map MAP-TO-F
6. Verifying the connectivity
HDRBR01#ping 192.168.250.210 —Tunnel10 interface of STFVVPN05
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.250.210, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 152/164/180 ms
HDRBR01#sh crypto isakmp sa —Phase 1 it has to be QM_IDLE
IPv4 Crypto ISAKMP SA
dst src state conn-id status
1×3.97.1×3.88 10.254.29.3 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
HDRBR01#sh crypto ipsec sa —–Phase-2, packets need to be encap and decap
interface: GigabitEthernet0/0
Crypto map tag: MAP-TO-F, local addr 10.254.29.3
protected vrf: (none)
local ident (addr/mask/prot/port): (10.254.29.3/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (1×3.97.1×3.88/255.255.255.255/47/0)
current_peer 1×3.97.1×3.88 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 14, #pkts encrypt: 14, #pkts digest: 14
#pkts decaps: 12, #pkts decrypt: 12, #pkts verify: 12
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 1
local crypto endpt.: 10.254.29.3, remote crypto endpt.: 1×3.97.1×3.88
path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0
current outbound spi: 0xF3D0D157(4090548567)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x51567CA3(1364622499)
transform: esp-des esp-md5-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 1, flow_id: 1, sibling_flags 80000040, crypto map: MAP-TO-F
sa timing: remaining key lifetime (k/sec): (4331701/2078)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xF3D0D157(4090548567)
transform: esp-des esp-md5-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 2, flow_id: 2, sibling_flags 80000040, crypto map: MAP-TO-F
sa timing: remaining key lifetime (k/sec): (4331700/2078)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
7. Running EIGRP over the tunnel
HDRBR01
router eigrp 224
network 192.168.250.209 0.0.0.0
network XXX —-Advertise other inside network into EIGRP
STFVVPN05
router eigrp 224
network 192.168.250.210 0.0.0.0
network XXX —-Advertise other inside network into EIGRP
8. Verifying EIGRP Neighborship
HDRBR01#sh ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(224)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 192.168.250.210 Tu0 14 00:03:11 1 3000 0 1
STFVVPN05#sh ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(224)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 192.168.250.209 Tu10 11 00:03:59 1924 5000 0 1
I hope this will help you in troubleshooting and configuring GRE over IPsec site to site VPN when a NAT device is in the path.
Comments (1)
Categories
Popular posts

Cisco Nexus Port Channel: Configuring ...
4 Apr 2024
Configure Rapid PVST on Cisco Nexus
5 Apr 2024
Palo Alto Exam Cost: PCNSA, PCNSE & More
28 Mar 2024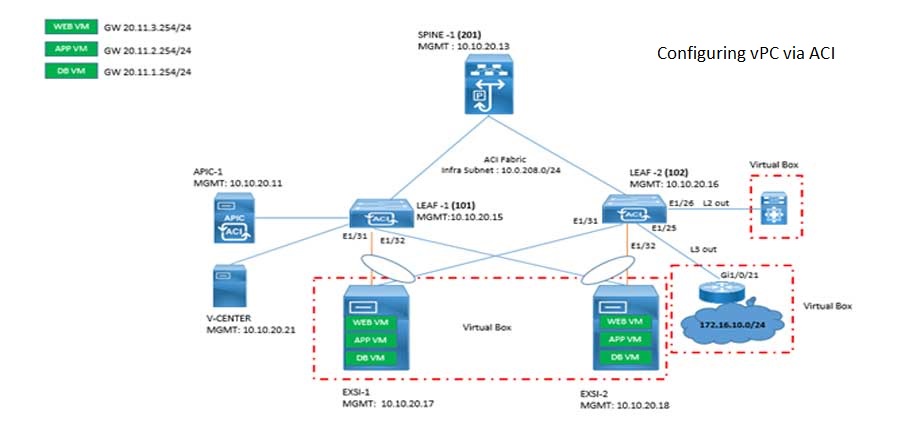
Cisco ACI VPC Configuration Task Steps
6 Jan 2024Recent posts

AWS Certification Path: Amazon Cloud
18 Apr 2024
SD-WAN Vendors Comparison: Choosing the ...
16 Apr 2024
CCNP Certification Cost and Exam Fees
12 Apr 2024
Configure Rapid PVST on Cisco Nexus
5 Apr 2024




This is an informative blog on IPsec vpn with full practical, seems it is taken from a production scenario. Please keep sharing such technical articles.